Bringing Cybercriminals to Justice
By Matt Windsor
 |
Watch Gary Warner explain how the UAB Spam Data Mine is helping combat criminals and train the next generation of spam assassins. |
Gary Warner still stays up late looking for trouble, but these days the trouble usually comes looking for him. Russian mobsters burst in a few hundred times per hour. Nigerian Yahoo Boys visit regularly, too. Day and night they’re at it, probing the UAB computer scientist for weaknesses, hoping to win him over with promises of drugs, money, and deeply discounted watches.
Judging by the contents of his e-mail inbox, Gary Warner may be the most gullible man on the Internet. Cut-rate diplomas? Cheap mortgages? Free iPods? Warner gets upwards of 25,000 unsolicited commercial e-mails every day, yet he’s always hoping for more. His dream is to get on every junk mailing list on the planet.
This may sound like a dubious obsession for a man on the cutting edge of computing—a high-tech craftsman wallowing in the lowest form of digital sludge, like Proust working on Mad Libs. But Warner is not slumming for the fun of it; he has a master plan for all this spam. Armed with massive computing resources, a group of eager students, and the services of a data mining expert, UAB’s director of research in computer forensics wants to put criminal spammers out of business for good. And if he can only get his hands on a few billion more e-mails, he just might do it.
Warner estimates that the volume of spam worldwide has increased 65 percent since January 2002; barely 10 percent of all e-mail today is legitimate. In April, UAB’s servers processed 24 million e-mail messages, and two-thirds of these were instantly identified as spam. But they weren’t all thrown away—a million or so went to Warner, who is using them to take a bite out of cybercrime.
The Man With the Plan
Welcome to the front lines of the spam war, which happen to be wherever Gary Warner is. This could be his windowless ground-floor office in Campbell Hall, lined with mementos from the FBI and books with titles like Secrets of Hackers EXPOSED. Or it could the mini war room down the hall where he teaches students how to shut down fraudulent “phishing” Web sites—clever reproductions of Amazon.com, eBay, and online banking sites that are designed to lure unsuspecting users into revealing their personal information.
 |
Listen to UAB spam expert Gary Warner (above) discuss the evolution of online crime and the latest security threats. |
Just as often, Warner carries on the fight at his house. “Cybercrime is an around-the-clock business,” he says. “On a typical day, I’ll get up about an hour and a half before my family and go check new phishing sites.” Then it’s off to work, where he conducts research and trains students in the art of computer security. In the evening, after the kids are in bed, he’s back at it again. “I documented 170 counterfeit bank Web sites between midnight and 1:00 this morning,” he says, describing an average night’s work.
Warner’s credibility in the computer security community is such that antivirus companies will update their software based on his recommendations alone—a rare measure of respect. Agents from the FBI and many international law enforcement agencies are regular followers of Warner’s blog, CyberCrime & Doing Time, and his investigations often provoke phone calls that begin like this: “Gary, I read your post on the Turkish Hotmail scam, and we want to know...”
Today’s spam is much more vicious than it used to be, Warner says. Take the BBB Virus for example. Last October, corporate officers at many large financial institutions and defense contractors started receiving official-looking e-mails from the Better Business Bureau, notifying them that a complaint had been lodged against their organizations. The complaint itself was attached to the e-mail, but in type too tiny to read. Not to worry: The message contained a helpful link so the recipient could download and print it out.
This would be a mistake. Anyone fooled into clicking on the link immediately downloaded a nasty piece of software that investigators later dubbed the BBB Virus. The first thing the BBB Virus does is to disable antivirus software on the victim’s computer. Next, it alters the computer’s Internet browser so that anyone who types in the addresses www.bankofamerica.com or www.ebay.com is redirected to criminal replicas of those popular sites instead. It starts a “keylogger” program, which records everything the user types. Then it rifles through the hard drive, copying all the Microsoft Office documents and e-mail addresses it can find, and sends those to its criminal masters. Finally, it starts searching for other nearby computers to infect.
Warner figured out how BBB operates and helped spread the word, advising antivirus companies on how they could alter their software to detect it. This kind of work has earned him an international reputation. In a recent profile, PC World magazine dubbed him the “White Knight of Phish-Busting.”
The Root of All Evil
The White Knight of Phish-Busting is the man you call when you have a sensitive problem and you don’t know how to fix it. “Yesterday, a large bank based in this area contacted me,” Warner says. “They had phishing sites in Korea that they couldn’t shut down. I have really good contacts in Korea, people I’ve met with face to face, so I called one of them and said, ‘Hey, it’s Gary. Could you shut these sites down for me?’ And they were able to go in, speak to the Internet service provider in Korean, and get those sites taken care of.”
 |
Since he joined UAB in 2007, Warner’s phish-busting usually begins with a trip into the UAB Spam Data Mine, a vast and growing collection of millions of pieces of electronic junk. Several times a day, Warner leads forays into its murky depths to see what foul concoctions the world’s spammers have devised. Part early-warning system, part forensic exhibit, part training ground for future crimefighters, the Spam Data Mine is still in its infancy. But it could eventually become the trap that nets the world’s most dangerous spammers.
“Most spam research right now is focused on one problem: How can I filter spam so that the guy who is reading his e-mail doesn’t see it?” says Warner. “We want to solve a different problem. We want to catch the criminals sending the spam, and catch so many criminals that when someone is trying to decide on a career choice, he’s going to say, ‘Hackers go to jail; I shouldn’t do that.’”
Contrary to popular belief, Warner says, nothing online is untraceable—if you have the time and resources to track it, which most investigative agencies don’t. “We’re trying to automate the whole process of figuring out which spam is worth tracing,” says Warner. “We want to be able to say, ‘Out of these billion spam messages, the top one came from this group of computers—if you investigate them, you can cut spam significantly and catch a guy who has probably made tens of millions of dollars.’”
Is there really that much money in the spam game? Yes; according to a 2007 report from Ferris Research, spam’s economic impact has hit $100 billion worldwide and $35 billion in the United States alone. Some of those billions come from people who actually are willing to buy pirated software and magic diet potions online. But that is the old, less-profitable version of spam—a 21st-century version of direct mail marketing, albeit with a shadier twist.
The real money in spamming, however, comes from out and out theft. Identity thieves, blackmailers, purveyors of illegal drugs—nowadays, their favorite method of attack is e-mail. [Listen to Warner explain the evolution of computer crime and the latest in high-tech spying in an audiocast here].
“Spam is the root of all evil,” Warner says. “In so many different kinds of cybercrime, it is a big piece of the puzzle. There are phishing spams that are pretending to be from your bank. If I’m going to do identity theft against you, I might e-mail you a link to a Web site, and if you visit that Web site, it will download software to your machine that allows me to steal everything you type. The viruses that destroy our data and steal trade secrets—even the e-mails by which foreign governments are spying on our military computers—a lot of that is based on someone getting a spam message and clicking on it.”
Plumbing the Depths
Modern spamlords aren’t interested in getting you to reach into your wallet for a $20 bottle of pills; they would much rather just take your wallet instead. Stealing credit card numbers is one goal. But they’re also looking for names, phone numbers, Social Security numbers—all the things they’ll need to open new charge cards, car loans, and mortgages using your credit as collateral.
Warner has clocked plenty of time exploring the seedy underbelly of the Internet. Lurking in criminal chat rooms, he comes away with the unsettling details that make him a sought-after speaker at computer security conferences from Seattle to Singapore.
 |
His lectures are full of characters like the Russian hacker “MrBond,” who has 48 million identity records for sale—full sets of names, Social Security numbers, places of birth, home and cell phone numbers, everything you would need to open a credit card—all for $4 each. Then there is “xsash,” who boasts that for $300 he can shut any Web site down for 24 hours. Monthly and hourly rates are also available.
Once, the MrBonds of the criminal netherworld were lone wolves, working alone in their parents’ basements. Today, the watchdog group Spamhaus “believes that 80 percent of all spam comes from 200 spammers,” Warner says. And even these 200 often operate together in packs, according to Spamhaus: the Russian Business Network, India’s Data Champions, Australia’s Global Web Promotions, and dozens of American crews such as Interactive Adult Solutions and EZ Shoppin.
Some groups are strictly into spamming; others are not so picky. In fact, the same underworld figures involved in offline prostitution, extortion, and money laundering have invested heavily in computer fraud, says Warner: “Most cybercrime today is the work of the Russian mafia; that’s just the way it is.”
Re:Action
Although he has many interests—haiku, genealogy, caffeine, the collectible card game Chron X—Warner has an insatiable appetite for spam. And he is doing his best to pass on the taste to his students. Several days a week, a small group crowds into a tiny, windowless room in Campbell Hall to do battle with the evil geniuses of the Russian mafia. Violating every rule of Internet self-defense, they do what the rest of us never should: open spam e-mails, click on the links, and follow them down the data stream into the heart of darkness.
 |
Warner with students |
There are monsters here. As Warner’s crew clicks its way through the bulging depths of the Spam Data Mine, nasty viruses, sneaky Javascripts, and Trojan horses of every size, shape, and breed come charging out. It’s enough to fry a lab’s worth of hardware in no time, but these are no ordinary computers. Hermetically sealed off from UAB’s main computer network, they are designed to capture every line of rogue code, examine it, and digitally preserve it in a perpetual forensic exhibit. Then, in a session that is part pathology and part epidemiology, the spam team inspects its prey.
On a recent afternoon, their mission was to tackle a possible new variant of the Storm Worm, one of the most dangerous criminal enterprises on the Internet. Storm is a “botnet,” a massive collection of captive computers, sometimes tens of thousands strong, that have all been infected with a virus that puts them under the control of a hacker. Research suggests that the top six botnets are responsible for 85 percent of all spam messages, and the Storm Worm is one of the biggest of them all.
In late June, Warner’s group started to see a flood of spam with subject lines based on hot items in the news: “Brad Pitt confesses to betrayal,” “McCain suffers heart attack,” “Oil falls below $100 a barrel.” These provocative lines were paired with equally intriguing (and apparently random) body text in the e-mails-“Kobe Bryant traded to Toronto in latest blockbuster trade”—with a link to a video. The video never materialized, of course; instead of seeing a clip, duped visitors got a spam-sending virus for their pains.
Warner quickly spread the word about the new attack on his blog. “About the same time—it may be coincidence, but we like to think not—the first wave of the campaign ended and a new one began,” he says. “And after we raised publicity on that new version, it changed again.”
The spammer was trying to evade detection, but Warner and his students discovered unmistakable signatures that tied the versions together. One benefit of this breakthrough was that they could track the fearsome spread of the virus. “By the end of the first week in July, as much as 25 percent of all the e-mail we received each day was sent by machines infected by this virus,” Warner says. If the growing Spam Data Mine is a statistically valid sample of the worldwide state of junk e-mail—and testing indicates that it is—then this one campaign became the most prolific spam source on the planet in less than a month.
The UAB research also gave law-enforcement agencies the proof they needed to link hundreds of apparently different spam messages to the same culprit, allowing them to “move closer to identifying the actual individual behind this campaign,” says Warner.
This external assistance is a boon for the overworked officials tasked with catching the world’s cybercriminals. It’s also great experience for the next generation of Internet crimefighters. “Our students actually work on live viruses that are part of active law-enforcement investigations,” Warner says. “And we’re working with the people who are leading those investigations in various federal agencies. They know when we’re going to be in the lab, and they’ll ring my phone as soon as we’re done and say, ‘What did you find out?’
“That’s why I’m at UAB instead of a security company,” Warner continues. “I could make a big difference in a security company helping them do a better job of analyzing viruses or finding phishing sites, but I didn’t want to just shut down sites or write a better tool—I wanted to train people.”
To Catch a Spammer
Warner’s students soon master the basics of cybersleuthing; they can rapidly “work” a phishing crime scene, collecting all the information they need to get a malicious site shut down in 10 minutes.
Unfortunately, the wheels of justice don’t turn that fast. By the time you track down the right people and get the proper authorizations, “it may take you four or five hours to actually get a site shut down,” Warner says. “And in one minute, the spammers can have another one up.” Last fall, the UAB Spam Team investigated 23,000 phishing sites attacking 243 different financial institutions. The trouble is, phishers set up new sites at the rate of 20,000 per month.
An example of a “phish”—a fake Web site used to steal the personal information of unsuspecting Internet users
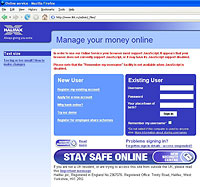 |
An example of a “phish”—a fake Web site used to steal the personal information of unsuspecting Internet users |
Of course, shutting down even one phishing site can stop innocent computer users from losing money. But the crime is so pervasive that it’s a little like plugging leaks in a faltering dam; for every hole that’s closed, four new ones open. It’s so bad that many in the computer industry are waving the white flag. “Unfortunately, spam has achieved a ‘certainty’ status along with death and taxes,” declared a recent online editorial from CNET News. “Fighting seems hopeless at this point. The best bet is to buy the best protection you can afford and move on.”
But Gary Warner is not interested in moving on. He has been fighting back against hackers since his days at Samford University in the early 1990s, when he was a young protege of UAB computer scientist Landy Manderson. Later, at Birmingham-based utility conglomerate Energen, Warner hooked up with the feds, helping the FBI track down a hacker who had broken into sensitive computers at NASA. (The hacker had earlier wreaked havoc on Energen.) He was a founder of the Birmingham chapter of InfraGard, an organization that brings together computer security professionals and law-enforcement officials.
After years of neglect and sentences that were little more than slaps on the wrist, law-enforcement agencies nationwide are becoming more aggressive in prosecuting cybercrime. Alan Ralsky and Robert Soloway, the “Spam Kings” who once boasted to newspapers of their lavish lifestyles, were recently indicted after lengthy investigations. And in May, the FBI, IRS, and FDA combined to arrest a group of Florida men accused of making $77 million by selling controlled pharmaceuticals online.
Who Falls for Spam?With all the warnings out there, why would anyone knowingly click on a spam message? Two reasons, Gary Warner says: fear and greed. “Different people will fall for different tricks,” he explains. “Maybe I send you an e-mail message that says, ‘We’ve noticed that your credit card was used in Romania. If you haven’t been to Romania, click here.’ Some people will have a panic reaction to that. Without thinking, they will click on the link. The thing is, nobody has used your credit card in Romania—not yet. They will after you give them all the information, though.” But some people say, “‘I know I should never click on anything,’” Warner continues. “So if I’m a spammer, how am I going to steal their money? What if I give them a telephone number instead? You see a phone number in an e-mail; you check and see that it has a 334 area code. That’s Montgomery, and your bank is in Montgomery. So you dial, and they answer the phone, ‘This is your bank; how can I help you?’ Actually, your call has been routed over the Internet to a spammer overseas. You tell them, ‘Well, I got this e-mail.’ And they say, ‘Thank you for calling! We’re concerned about the safety of your account. Just to verify that this is legitimate, please give us the last four digits of your Social Security number.’ You give them your number, and they say, ‘That matches what we have on file for you. Here’s what we need: We need to know if you’ve changed your online password lately. What’s the last password you had? Okay, it looks like the criminal hasn’t used your account. Thanks for calling!’” Some people are lured by the panic attack, Warner says, “and some people go for greed.” A recent spam message making the rounds purported to be from a major bank, promising account holders $80 in return for taking a quick survey. Sure enough, says Warner, a 10-question survey appeared, followed by a new screen. “It said, ‘In order to deposit the money to your account, please enter your credit card number, your name, the card’s expiration date, the three-digit number on the back of the card, and your electronic signature. We suggest you use your ATM PIN as your electronic signature because it’s easy to remember.’” And someone actually fell for this? Sure, says Warner. “Some people tell us, ‘Well, I knew that might have been fake, but what if it was real? I would have just thrown away $80, and if it was fake, and somebody steals my money, I’ll just file a police report and get my money back.’” |
Many phishers attack the United States from overseas, counting on lenient local governments or the sheer red tape of international law enforcement to protect them from prosecution. But the FBI has made inroads, says Warner. Working with a new Romanian cybercrime task force, the agency apprehended more than 50 phishers this summer. “When we presented a phishing case to law enforcement, they used to tell us, ‘Well, they’re probably in Romania; that’s the end of it,’” Warner says. “Now the answer is, ‘Okay, let’s go catch them!’”
The situation around the world has improved by “leaps and bounds,” Warner continues. “But we’re still a long way from success. It used to be that only 1 percent of hackers went to jail, and now it’s maybe 3 percent. So we’ve tripled the number of people who go to jail for computer crimes in the last couple of years. Compare that to bank robbery, where 99 percent of bank robbers get caught within 14 days. People who do phishing sites, 95 percent of them never get caught—we’ve got to change that.”
Enter the Machine
The problem is not tracing any individual piece of spam: It is connecting the biggest, nastiest spam campaigns. “On a given day, we’ll look at between 100 and 400 counterfeit bank Web sites,” says Warner. “But we don’t really want to create 400 different cases every day. Nobody has the staff to deal with all these phishing sites, so they just ignore them.”
In reality, half of those 400 sites may be linked to a single spammer. And he may be up to more than phishing, Warner says. “The same guy who is selling Cialis may also be stealing Bank of America passwords and counterfeit Microsoft software. And we’re one of the only places that is comparing all the messages and saying, ‘Hey Microsoft, Bayer, and Bank of America—you need to be talking to each other, because this is the same criminal.’”
But making connections is not enough. Law-enforcement agencies, like everyone else, must set priorities, and prosecuting cybercrime cases is a slow, unglamorous business. “The real challenge is, can we get anyone interested enough to say, ‘Instead of going after the guy who stole $400,000 in this embezzlement scam, I’m going to go find out why you’re seeing so much counterfeit watch spam.’ Right now, it might take 200 man-hours to track down a spammer. If we could make that two hours, they would say, ‘Yeah, that’s worth it.’ I don’t know that we can, but we’re going to make it a lot easier than it is today.”
To reach that goal, Warner and UAB data mining expert Alan Sprague, Ph.D., are working on the Deep Thought of the spam game, a single-minded computer capable of finding the throbbing heart of the spamiverse—and ripping it out. Essentially, the task is to sort the millions of messages in the Spam Data Mine “into piles, with each pile containing all the messages written by one spammer,” says Sprague. “Then you know that the biggest piles are made by the biggest spammers, and law enforcement has the most interest in the biggest piles.”
In other words, the more spam Gary Warner can collect, the easier it will be to pinpoint the big gangs responsible and to identify the computers that are hosting their criminal Web sites. With a large enough data set, Warner says he could give law enforcement agencies real-time updates on the current greatest threats on the Net. “We will be able to help prioritize law-enforcement decisions,” he explains. “We’ll be able to say, ‘If you’re going to go after one spammer, this is the one who’s sending the most spam.’”
Thanks to significant funding from the National Institute of Justice; Microsoft; and David Barber, the district attorney for Alabama’s 10th Judicial Circuit, Warner says he has the resources to build a machine capable of handling hundreds of millions of e-mails per day. The trouble is, he doesn’t have near that much e-mail. So he’s working with lawyers to find ways for public-spirited companies to volunteer their junk mail to the cause. “We have the computer; we have the technology; we have the money—what we need is a whole lot of spam,” he says.
“That doesn’t mean you should send Gary all your spam,” Warner adds hastily. Forward him an e-mail from your inbox right now, and “what I’ll learn is that you sent the e-mail to me. What I won’t learn is who sent it to you,” he says. Only a “forensically clean copy of an e-mail” will work as evidence. Someday, if he can “find a student willing to take that on as a programming project,” Warner hopes to be able to solicit spam contributions directly from the public.
On the other hand, “if there’s any organization that would like to give me a hundred million e-mails a day, I would love to have them.”