 Passwords are a common security measure to protect personal information, but they don’t always prevent hackers from finding a way into devices. UAB researchers are working to perfect an easy-to-use, secure login protection that eliminates the need to use a password — known as zero-interaction authentication.
Passwords are a common security measure to protect personal information, but they don’t always prevent hackers from finding a way into devices. UAB researchers are working to perfect an easy-to-use, secure login protection that eliminates the need to use a password — known as zero-interaction authentication.
At UAB, this research is led by Associate Professor Nitesh Saxena, Ph.D., co-leader of the Center for Information Assurance and Joint Forensics Research.
In zero-interaction authentication, access is granted when the verifying system can detect the user’s security token — such as a mobile phone or a car key — using an authentication protocol over a short-range, wireless communication channel, such as Bluetooth.
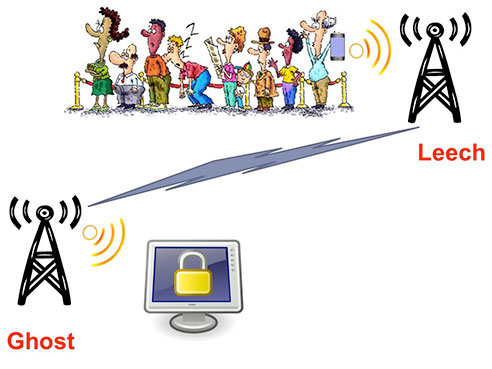
However, existing zero-interaction authentication schemes are vulnerable to relay attacks, commonly referred to as ghost-and-leech attacks, in which a hacker, or ghost, succeeds in authenticating to the terminal on behalf of the user by colluding with another hacker, or leech, who is close to the user at another location, Saxena said.
| The goal of UAB's research is to improve security measures that could protect against relay attacks without affecting usability. |
The goal of UAB's research is to improve security measures that could protect against relay attacks without affecting usability. First, they examined four sensor modalities commonly present on devices: Wi-Fi, Bluetooth, GPS and audio. Second, they looked at ambient physical sensors: ambient temperature, precision gas, humidity and altitude. Each of these can help the system verify the two devices attempting to connect are in the same location and thwart a ghost-and-leech attack; when used in combination, they provide robust security, Saxena said.
Platforms that employ sensor modalities are available on many smartphones and they will likely become more commonplace in the near future, Saxena said.
“Users will be able to use an app on their phones to lock and unlock their laptops, desktops or even their cars, without passwords and without having to worry about relay attacks,” said Babins Shrestha, a UAB doctoral student and co-author on the papers.